
Derived mean vulnerability curves correlated with elastic 5 % damped... | Download Scientific Diagram

Elastic and IDC showcase the Future of Security in Finance on October 10th. Register now and stay ahead of the curve. | Gzim Xheladini posted on the topic | LinkedIn
Cloud Security] [Vulnerability Management] Vulnerabilities status endpoint · Issue #151878 · elastic/kibana · GitHub

Kyber Network Warns Elastic Liquidity Providers of Potential Vulnerability - Crypto News - Unchained

Tenable Unveils SaaS Platform that Redefines Vulnerability Management for Today's Elastic IT Environments | Business Wire

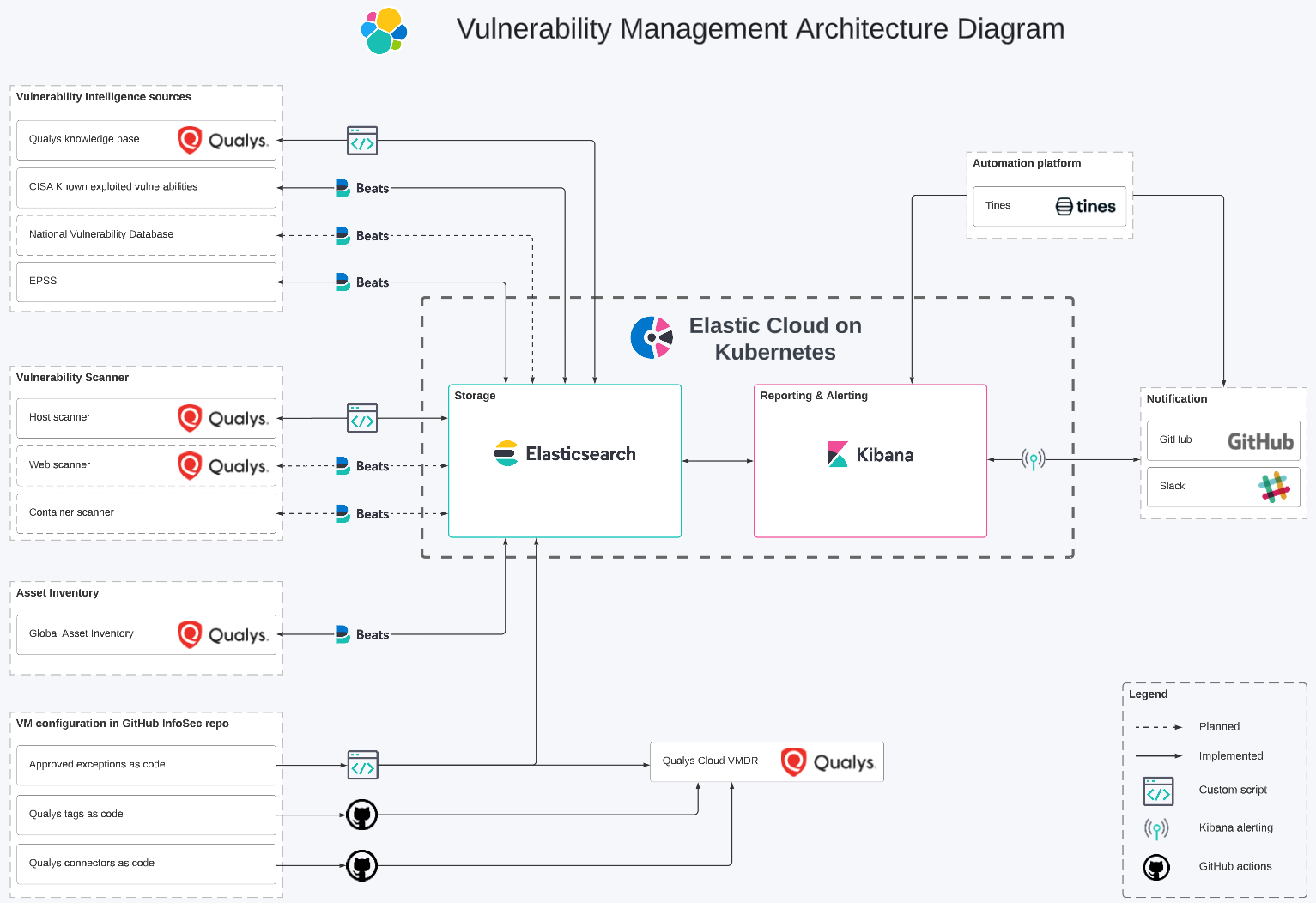

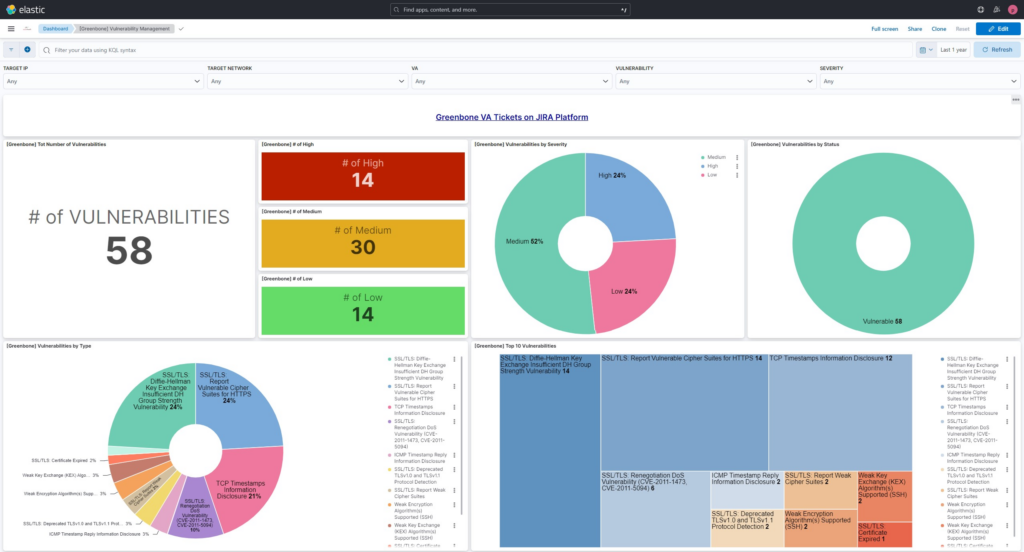







![Cloud Native Vulnerability Management Dashboard | Elastic Security Solution [8.11] | Elastic Cloud Native Vulnerability Management Dashboard | Elastic Security Solution [8.11] | Elastic](https://www.elastic.co/guide/en/security/current/images/vuln-management-dashboard.png)


