How to build a CI/CD pipeline for container vulnerability scanning with Trivy and AWS Security Hub | AWS Security Blog
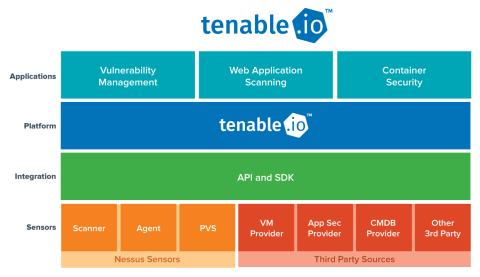
Tenable Unveils SaaS Platform that Redefines Vulnerability Management for Today's Elastic IT Environments | Business Wire
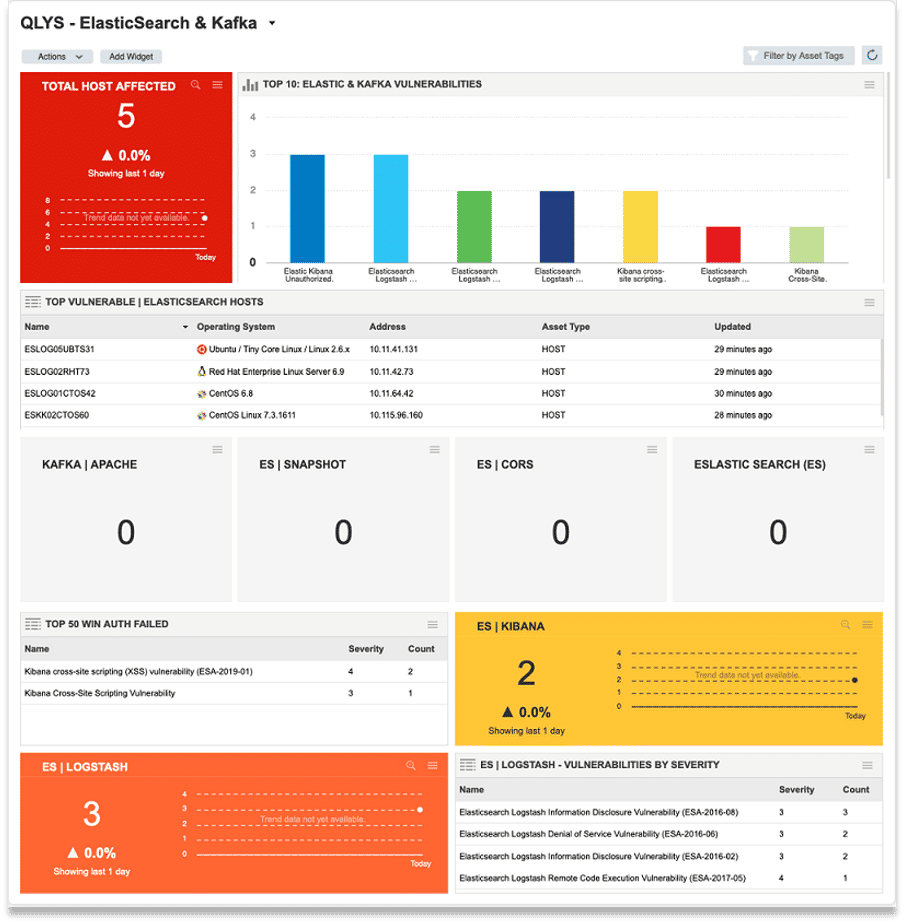
GitHub - HKcyberstark/Vuln_Mod: Vulnerability Assessment Module - OpenVas with Elastic stack using VulnWhisperer

GitHub - HKcyberstark/Vuln_Mod: Vulnerability Assessment Module - OpenVas with Elastic stack using VulnWhisperer

⠀ Aaron Jewitt on LinkedIn: Detection Engineering and Vulnerability management at Elastic | AMS User…






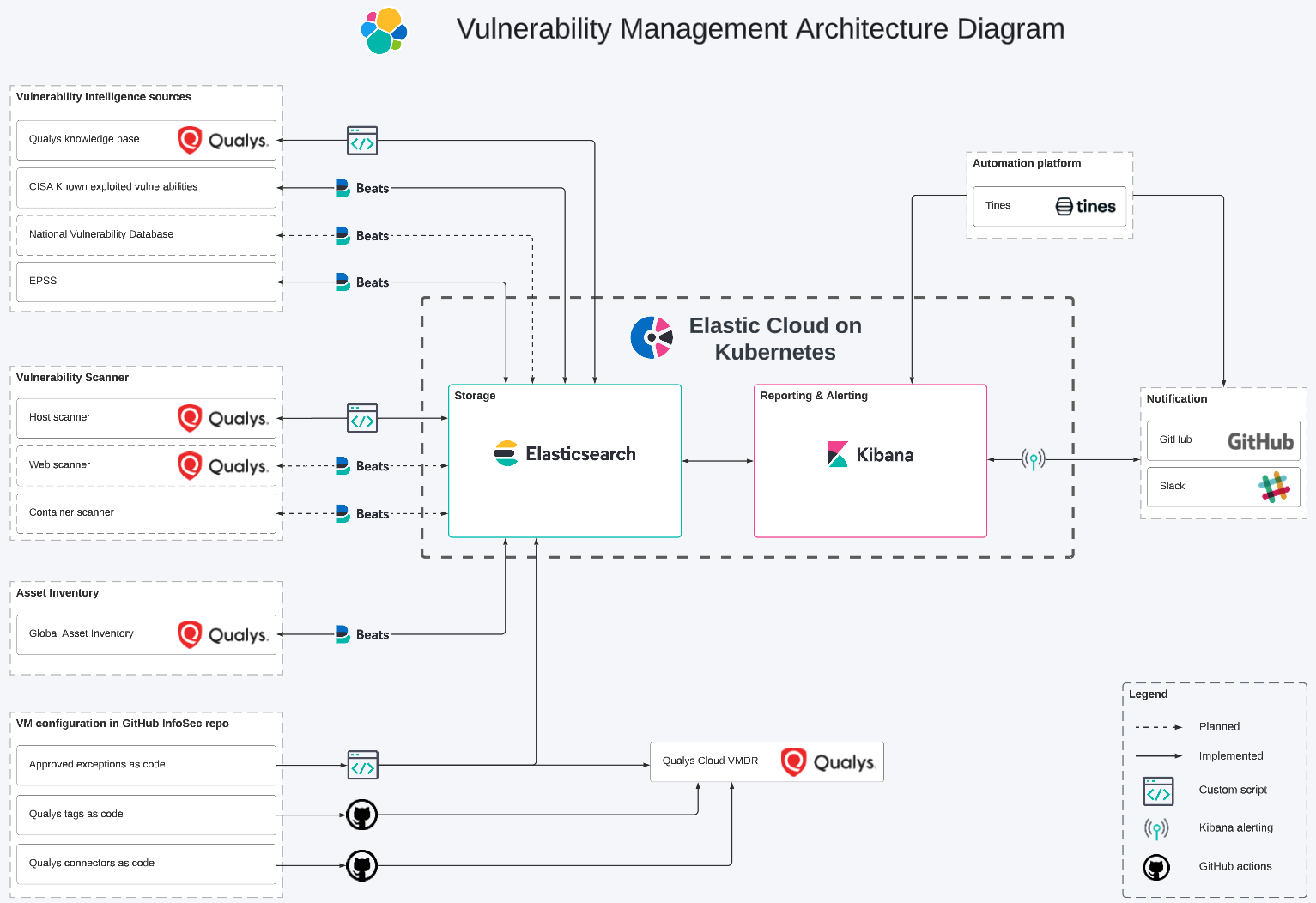



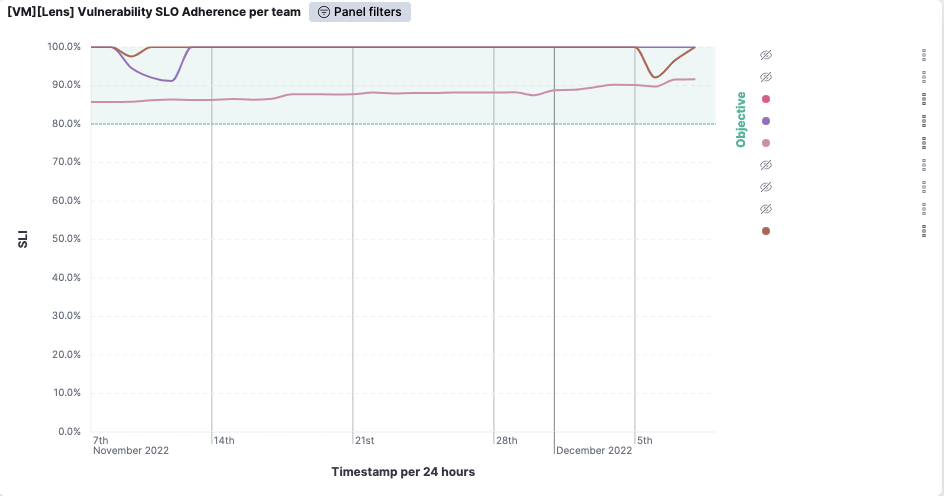
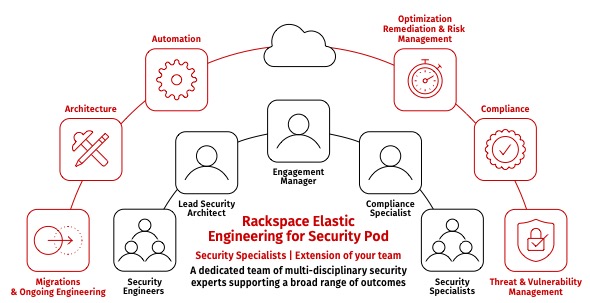
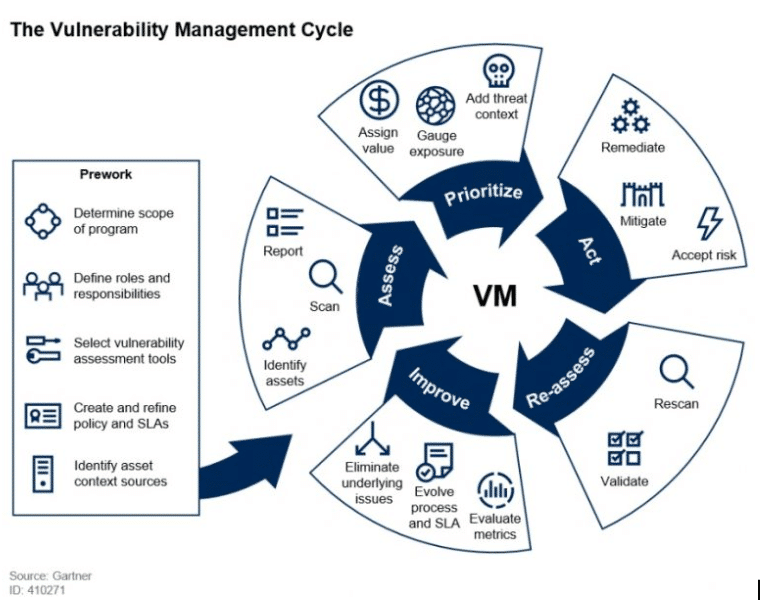

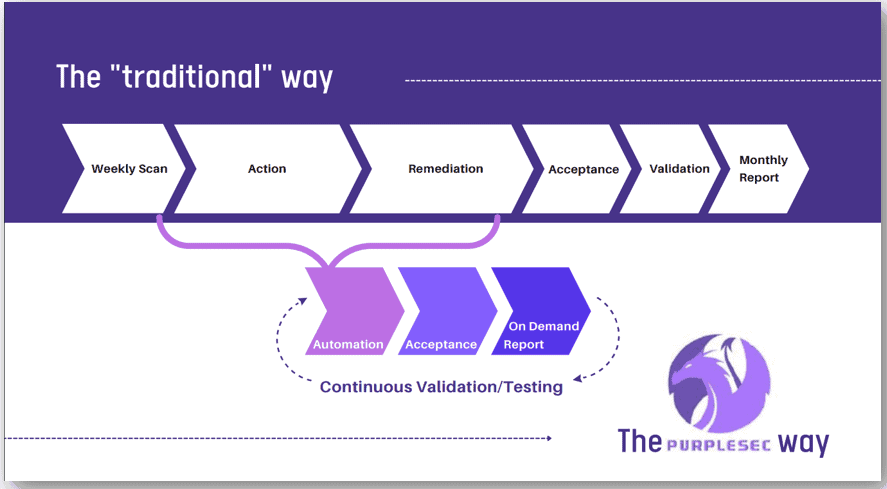
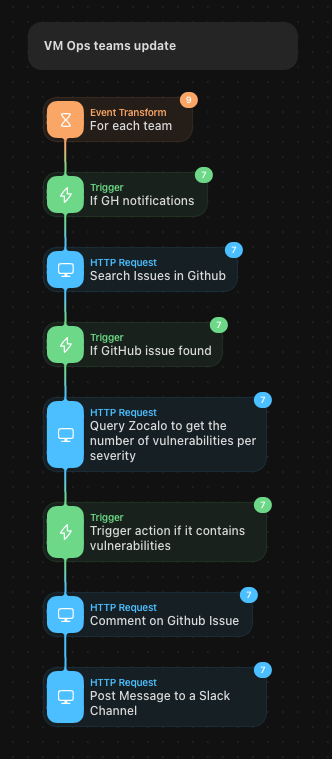
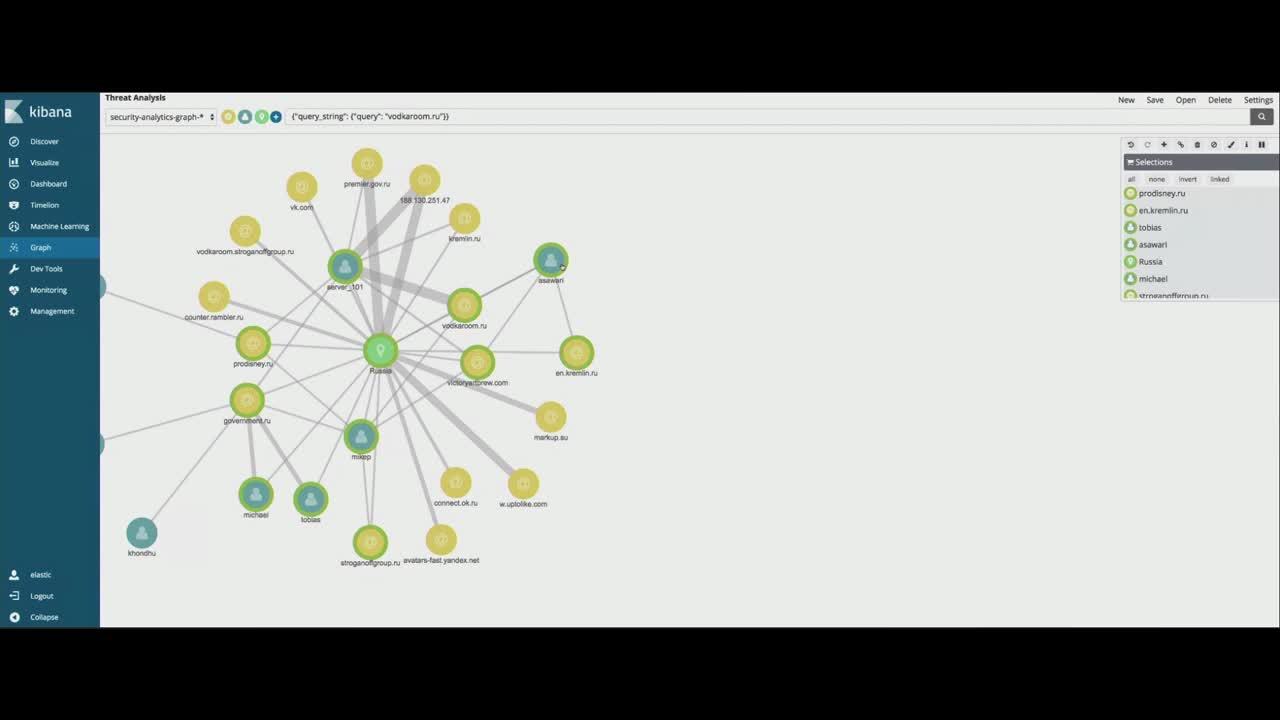
.png)